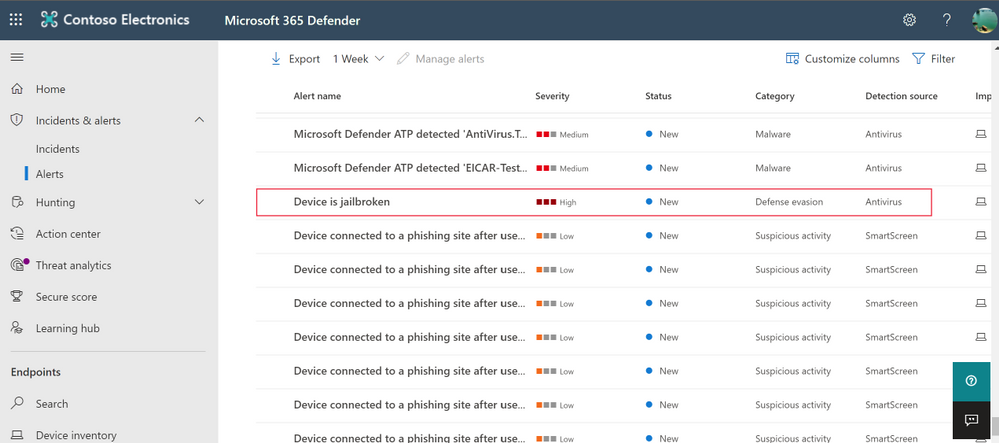
Your Jailbroken iPhone Is a Threat to Your Company, Says Microsoft
For those that want to truly personalize their phone, jailbreaking has always been an excellent way to make your device truly yours. However, Microsoft has released an update to Windows Defender for Endpoint that will sound the sirens if it detects a jailbroken iOS phone on a company network. Microsoft’s Newfound Hatred Of Jailbroken iOS Devices […]
Continue Reading